第一次在crypto中做到tea加密的题目,在此记录一下
TEA简介:
“TEA”的全称为“Tiny Encryption Algorithm”,TEA算法也叫微型加密算法
加密流程:
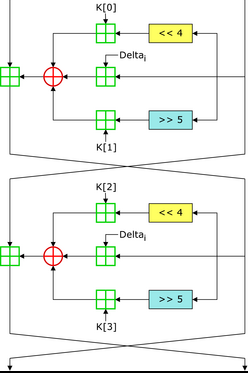
加解密代码演示:
1 | void Encrypt(long* EntryData, long* Key) |
解密思路:
1 | x +=xxx |
解密代码如下:
1 | void Decrypt(long* EntryData, long* Key) |
例题:
newstarctf 2024 茶里茶气:
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import * |